 官方公众号
官方公众号
 商务合作
商务合作
晚上好,同学们!USG防火墙上NAT是最常用也最容易“差一点点就不通”的功能。
今天一篇覆盖出网SNAT、服务器发布DNAT、双向NAT、地址池与easy-ip的选型,让你上线不踩坑。
今日文章阅读福利:《网络工程师手册》
扫添加小助理微信,备注【网工】,即可获取。
一、NAT有哪些类型?选什么?
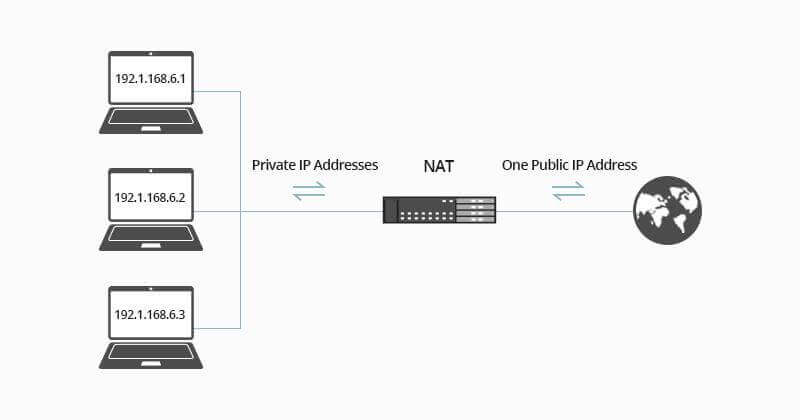
· 源NAT(SNAT):内网出互联网(办公上网、访问云)
o easy-ip:最简单,直接用出接口公网IP做SNAT
o 地址池:多公网地址,便于并发/审计/策略细分
· 目的NAT(DNAT/服务器发布):把公网端口映射到内网服务器
o nat server简洁直观;或用nat-policy细粒度控制
· 双向NAT/策略NAT:复杂场景(双活机房、重叠网段)
· 回流/发夹(hairpin NAT):内网访问公网域名回到内网服务器
二、基础拓扑与规划
· USG接口:
o GE0/0/1:Trust 192.168.10.1/24(内网)
o GE0/0/2:Untrust 100.64.1.2/30(公网/上联)
· 业务:
o 办公网出网:SNAT easy-ip
o 发布Web:公网100.64.1.2:80→内网192.168.10.100:80
三、快速配置(USG,基于nat-policy与安全策略)
1) 接口与安全域
[USG] interface GigabitEthernet0/0/1
[USG-GigabitEthernet0/0/1] ip address 192.168.10.1 255.255.255.0
[USG-GigabitEthernet0/0/1] quit
[USG] interface GigabitEthernet0/0/2
[USG-GigabitEthernet0/0/2] ip address 100.64.1.2 255.255.255.252
[USG-GigabitEthernet0/0/2] quit
[USG] firewall zone trust
[USG-zone-trust] add interface GigabitEthernet0/0/1
[USG-zone-trust] quit
[USG] firewall zone untrust
[USG-zone-untrust] add interface GigabitEthernet0/0/2
[USG-zone-untrust] quit
2) 出网SNAT(easy-ip)
[USG] nat-policy
[USG-nat-policy] rule name OUT-EASYIP
[USG-nat-policy-rule-OUT-EASYIP] source-zone trust
[USG-nat-policy-rule-OUT-EASYIP] destination-zone untrust
[USG-nat-policy-rule-OUT-EASYIP] action source-nat easy-ip
[USG-nat-policy-rule-OUT-EASYIP] quit
[USG-nat-policy] quit
3) 服务器发布DNAT(端口映射)
方式A:nat server(简单直观)
[USG] nat server protocol tcp global 100.64.1.2 80 inside 192.168.10.100 80
方式B:nat-policy(细粒度)
[USG] object-group service web
[USG-obj-grp-service-web] service tcp destination-port eq 80
[USG-obj-grp-service-web] quit
[USG] nat-policy
[USG-nat-policy] rule name DNAT-WEB
[USG-nat-policy-rule-DNAT-WEB] source-zone untrust
[USG-nat-policy-rule-DNAT-WEB] destination-zone untrust
[USG-nat-policy-rule-DNAT-WEB] destination-address 100.64.1.2 255.255.255.255
[USG-nat-policy-rule-DNAT-WEB] service group web
[USG-nat-policy-rule-DNAT-WEB] action destination-nat address 192.168.10.100
[USG-nat-policy-rule-DNAT-WEB] quit
[USG-nat-policy] quit
4) 安全策略(必须放行流量)
# 内网出网
[USG] security-policy
[USG-policy] rule name TRUST-TO-UNTRUST
[USG-policy-rule-TRUST-TO-UNTRUST] source-zone trust
[USG-policy-rule-TRUST-TO-UNTRUST] destination-zone untrust
[USG-policy-rule-TRUST-TO-UNTRUST] action permit
[USG-policy-rule-TRUST-TO-UNTRUST] quit
# 公网访问 Web 服务(DNAT 后回写 Trust)
[USG-policy] rule name UNTRUST-TO-WEB
[USG-policy-rule-UNTRUST-TO-WEB] source-zone untrust
[USG-policy-rule-UNTRUST-TO-WEB] destination-zone trust
[USG-policy-rule-UNTRUST-TO-WEB] destination-address 192.168.10.100 255.255.255.255
[USG-policy-rule-UNTRUST-TO-WEB] service tcp destination-port eq 80
[USG-policy-rule-UNTRUST-TO-WEB] action permit
[USG-policy-rule-UNTRUST-TO-WEB] quit
[USG-policy] quit
可选:地址池SNAT(并发/可审计)
[USG] nat address-group OUT-POOL 0 203.0.113.10 203.0.113.14
[USG] nat-policy
[USG-nat-policy] rule name OUT-POOL
[USG-nat-policy-rule-OUT-POOL] source-zone trust
[USG-nat-policy-rule-OUT-POOL] destination-zone untrust
[USG-nat-policy-rule-OUT-POOL] action source-nat address-group OUT-POOL
[USG-nat-policy-rule-OUT-POOL] quit
[USG-nat-policy] quit
常见坑
· 只做了NAT,忘了安全策略放行;或策略方向、目的地址(DNAT 后地址)配置不一致
· DNAT命中优先级被其他规则“盖住”
· 回流访问(内网通过公网域名访问内网服务器)需hairpin NAT/本地域名解析
四、验证与排错
# 会话与 NAT 命中
[USG] display firewall session table verbose
[USG] display nat session statistics
[USG] display nat outbound
[USG] display nat server
# 策略命中与顺序
[USG] display security-policy all
[USG] display current-configuration configuration nat-policy
# 抓包(有的型号支持接口抓包/镜像)
排错思路
· 先看策略是否放行,再看NAT是否转换,最后看路由回程是否正确
· DNAT场景,服务器默认路由须回USG;否则“单通不回”
最佳实践
· 易用优先:办公网出网优先easy-ip;需要区分与审计再用地址池
· DNAT尽量使用对象组管理服务/地址,便于变更
· 变更窗口测试:公网→内网、内网→公网、内网→本地域名(hairpin)
我们今天就分享到这,下次再见啦