 官方公众号
官方公众号
 商务合作
商务合作

本文将介绍在Kubernetes中使用containerd作为容器运行时如何去通过harbor拉取与上传镜像,在已有的harbor环境下,如何配置containerd去拉取harbor镜像。
/etc/containerd/certs.d/http://registry.harbor.com/
mkdir -p /etc/containerd/certs.d/registry.harbor.com/ containerd config default > /etc/containerd/config.toml
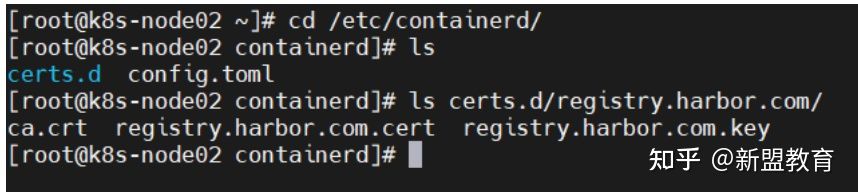
/etc/containerd/config.toml
......上面的配置略多,没有粘,只拿了下面有用部分 [plugins."io.containerd.grpc.v1.cri".registry] [plugins."io.containerd.grpc.v1.cri".registry.mirrors] [plugins."io.containerd.grpc.v1.cri".registry.mirrors."docker.io"] endpoint = ["https://registry-1.docker.io"] [plugins."io.containerd.grpc.v1.cri".registry.mirrors."registry.harbor.com"] #从这里开始添加,根据自己的环境,我这里harbor域名为 registry.harbor.com endpoint = ["https://registry.harbor.com"] [plugins."io.containerd.grpc.v1.cri".registry.configs] [plugins."io.containerd.grpc.v1.cri".registry.configs."registry.harbor.com".tls] insecure_skip_verify = true #跳过认证 ca_file = "/etc/containerd/certs.d/registry.harbor.com/ca.crt" #ca证书 cert_file = "/etc/containerd/certs.d/registry.harbor.com/registry.harbor.com.cert" #harbor证书 key_file = "/etc/containerd/certs.d/registry.harbor.com/registry.harbor.com.key" #密钥 [plugins."io.containerd.grpc.v1.cri".registry.configs."registry.harbor.com".auth] username = "admin" #harbor用户名 password = "Harbor12345" #harbor密码 配置截至到这里 [plugins."io.containerd.grpc.v1.cri".x509_key_pair_streaming] tls_cert_file = "" tls_key_file = "" [plugins."io.containerd.internal.v1.opt"] path = "/opt/containerd" [plugins."io.containerd.internal.v1.restart"] interval = "10s" [plugins."io.containerd.metadata.v1.bolt"] content_sharing_policy = "shared" [plugins."io.containerd.monitor.v1.cgroups"] no_prometheus = false [plugins."io.containerd.runtime.v1.linux"] shim = "containerd-shim" runtime = "runc" runtime_root = "" no_shim = false shim_debug = false [plugins."io.containerd.runtime.v2.task"] platforms = ["linux/amd64"] [plugins."io.containerd.service.v1.diff-service"] default = ["walking"] [plugins."io.containerd.snapshotter.v1.devmapper"] root_path = "" pool_name = "" base_image_size = ""
systemctl daemon-reload systemctl restart containerd
ctr --namespace=k8s.io images push registry.harbor.com/test/app:latest --skip-verify --user admin:Harbor12345 # --namespace=k8s.io 指定命名空间,不是必须,根据环境而定 # --skip-verify 跳过认证 # --user 指定harbor用户名及密码

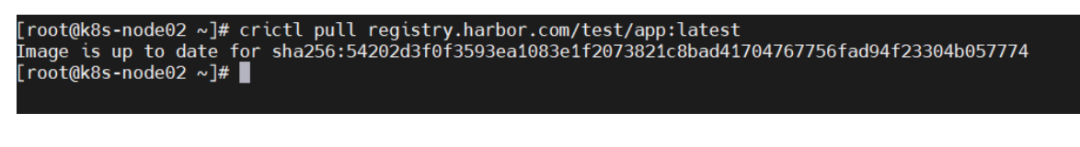
crictl pull registry.harbor.com/test/app:latest

推荐阅读
>>>新手必备-Linux系统安装配置+Xshell远程连接
运维界升职加薪必备的云计算技术,你学了吗?
学完高级运维云计算课程之后,你可以:
跨越90%企业的招聘硬门槛
增加70%就业机会
拿下BAT全国TOP100大厂敲门砖
体系化得到运维技术硬实力
技术大佬年薪可达30w+